Answers
Answer:
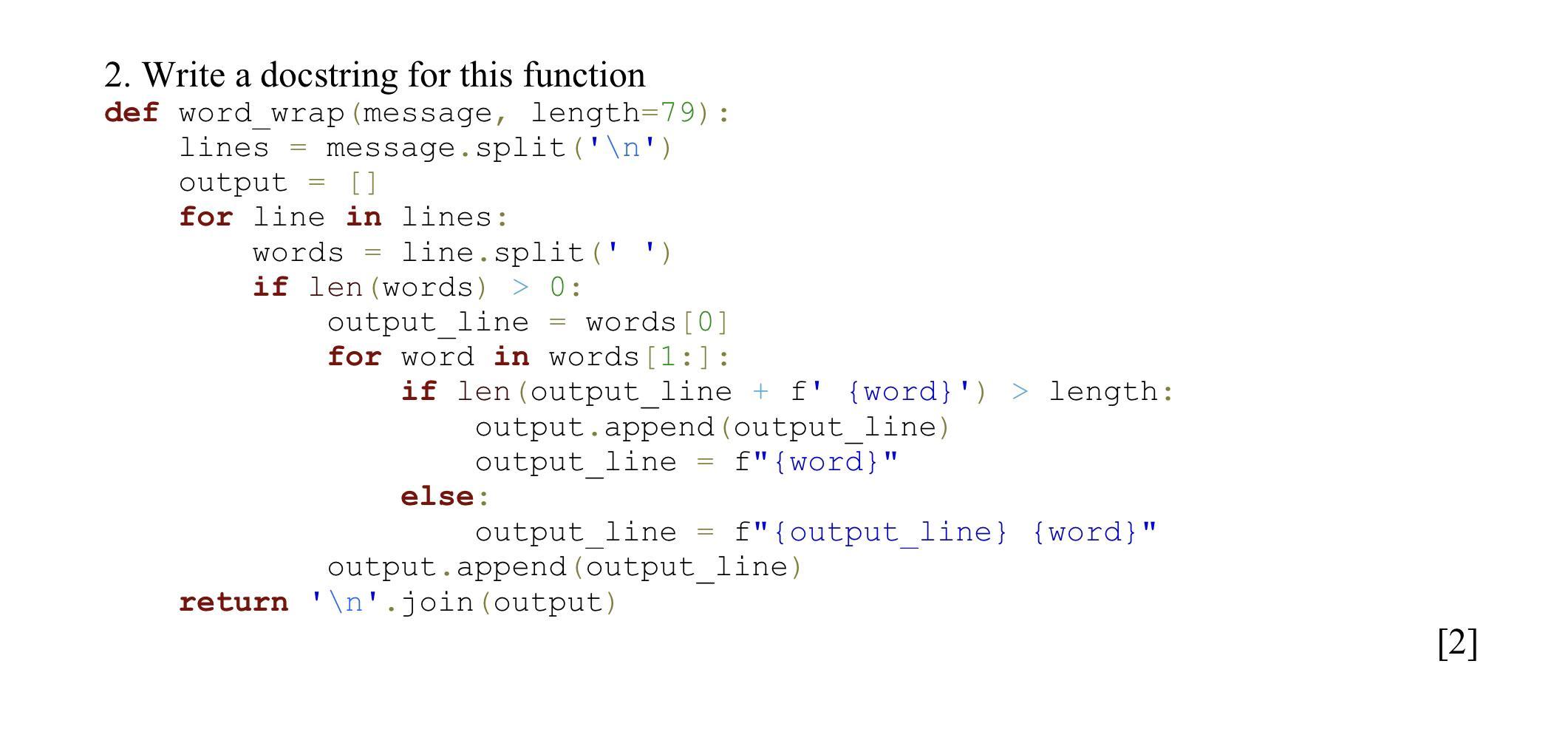
def word_wrap(message, length=79):
"""
Wrap a message to a specified line length.
Args:
message (str): The message to be wrapped.
length (int): The maximum line length. Default value is 79.
Returns:
str: The wrapped message.
"""
lines = message.split('\n')
output = []
for line in lines:
words = line.split(" ")
if len(words) > 0:
output_line = words[0]
for word in words[1:]:
if len(output_line + f' {word} ') > length:
output.append(output_line)
output_line = f"{word}"
else:
output_line = f"{output_line} {word}"
output.append(output_line)
return '\n'.join(output)
Related Questions
Insert the following records into the Manufacturer table. It is important that you insert the data exactly as shown below, including any commas or periods. Since this problem will require multiple SQL statements, you must end each statement with a semicolon.
Remember only submit the specific SQL statements required by the problem definition.ManufacturerID ManufacturerName Address City State PostalCode Phone
100 Classic Shoes Inc 521 Schaefer Ave Chino CA 91710 714-276-1180
101 All About Boots 80 Enterprise Avenue South Secaucus NJ 17094 102 Sports Footwear 22500 S. Vermont Ave Torrence CA 90502 310-783-1900
103 Fancy Feet LLC 910 S Los Angeles Street # 704 Los Angeles CA 90015 877-740-7732
Answers
The DDL command INSERT INTO table VALUES is used to add records to a table. Therefore, the Manufacturer table has 4 rows added to it.
What does a SQL do?
A database may be communicated with using SQL. It is the accepted language for relational database management systems, claims ANSI (American National Standards Institute). To change data on a database or to obtain data from a database, SQL statements are employed.
Is it difficult to learn SQL?
Because SQL is a very easy language, students may anticipate learning the fundamentals in two to three weeks. However, if you intend to use your SQL knowledge for job purposes, you'll likely require a greater degree of fluency.
Briefing:
INSERT INTO Manufacturer values(100, 'Classis Shoes Inc', '521 Schaefer Ave', 'Chino', 'CA', 91710, '714-276-1180');
INSERT INTO Manufacturer values(101, 'All About Boots', '80 Enterprise Avenue South', 'Secaucus', 'NJ', 17094, NULL);
INSERT INTO Manufacturer values(101, 'Sports Footwear', '22500 S. Vermont Ave', 'Torrence', 'CA', 90502, '310-783-1900');
INSERT INTO Manufacturer values(103, 'Fancy Feet LLC', '910 Los Angeles Street #704', 'Los Angeles', 'CA', 90015, '877-740-7732');
To know more about SQL visit:
https://brainly.com/question/13068613
#SPJ4
as in a physical store, merchandise in an online store can be grouped within logical departments to make locating an item simpler. T/F
Answers
True, unlike in a physical store, items in an online store can be sorted into logical divisions to make finding what you're looking for easier.
What are the major responsibilities of a provider of commerce services?For creating online business sites housed on the CSP's server, commerce service providers (CSPs) supply free or inexpensive electronic commerce software. Tools for catalog management are included in IBM WebSphere software components for B2C and B2B businesses.
What are the two primary functions of e-commerce?E-commerce refers to the buying, selling, or sending of goods, services, money, or data over an electronic network like the internet. These commercial exchanges can be B2B (business to business), B2C (business to consumer), C2C (consumer to consumer), or C2B (consumer to business).
To know more about store visit:-
https://brainly.com/question/7160004
#SPJ4
Which of the following functions does a consumer-grade access point combine into a single device? (Select two.)
NAT
AES
WAP
SSID
WPA
Answers
WPA and AES
Explain WAP and AESWPA served as a temporary WEP security upgrade during the development of the 802.11i wireless security standard. WPA was adopted formally one year before WEP was formally discontinued. Pre-shared keys (PSKs), most frequently referred to as WPA Personal, and the Temporal Key Integrity Protocol (TKIP; /tikp/) are used by the majority of current WPA apps. For the production of keys and certificates, WPA Enterprise uses an authentication server.WPA was a substantial improvement over WEP, but because its fundamental components could be installed via firmware updates on WEP-compatible devices, they still depended on vulnerable components.Lower compatibility standards are often no longer justified. Ten years ago, WPA2 certification became accessible. Any device produced after 2006 with a "Wi-Fi" label must support WPA2 encryption as WPA2 certification became mandated in 2006. It's been eight years since then! You should be good with merely selecting WPA2-PSK because your wifi-enabled gadgets are probably less than 8 to 10 years old (AES).To learn more about WAP refer https://brainly.com/question/26601084
#SPJ4
The signature for the nonmember < operator function for comparing two Rational objects is __________.
A. bool operator<(const Rational& r1, const Rational& r2)
B. bool
C. bool operator<(Rational r1, Rational r2)
D. bool operator(<)(const Rational& r1, const Rational& r2)
Answers
The Correct answer is C) bool operator<(Rational r1, Rational r2)
What is Boolean Operator?Boolean operators are straightforward words (AND, OR, NOT, or AND NOT) that are used as conjunctions in searches to combine or exclude keywords, producing more specialised and useful results. This should reduce time and effort spent by removing ineffective hits that be scanned before being thrown away.The number of records returned can be significantly decreased or increased by using these operators.Boolean operators are useful for speeding up searches by narrowing results to those that are more relevant to your needs and removing irrelevant or inappropriate results.Boolean operators may be used slightly differently by each search engine or database collection, or they may need to be entered in capital letters or with certain punctuation. The guide to the particular database can be discovered with the precise wording.To learn more about Boolean Operator refer to:
https://brainly.com/question/5029736
#SPJ4
The non-linearity of the logistic regression is obtained because of the use of a non-linear activation function. O True O False
Answers
False. The non-linearity of the logistic regression is obtained NOT because of the use of a non-linear activation function.
What is the reason for non-linearity of the logistic regression?
The most commonly utilised activation functions are non-linear functions. It makes it simple for a neural network model to adapt to diverse types of data and distinguish between distinct outputs.
When the classes can be distinguished in the feature space by linear bounds, logistic regression is typically utilised as a linear classifier. However, if we happen to have a better understanding of the form of the decision border, that can be fixed. As a linear classifier, logistic regression is well recognised and utilised. In order to distinguish between observations that belong to a class and all other observations that do not, it is utilised to create a hyperplane in feature space. As a result, the decision boundary is linear. It is simple to use logistic regression as a linear classifier because there are many reliable and effective implementations available (such as scikit-learn).
To know more about logistic regression refer:
https://brainly.com/question/27785169
#SPJ4
You need to deploy virtual machines in the cloud to support big data processing. The virtual machines must not be reachable from the Internet. Data processing summaries will be uploaded from the virtual machines to an on-premises database server. The on-premises network is already configured to allow incoming connections from the Internet. What should you do to allow the required functionality while maximizing security
Answers
On-site servers have virtualization deployed. A server is essentially running in your own server on your own premises when you virtualize it. Your establishment's server.
What virtual machines to an on-premises database server?It is possible to host solutions either on-premises (private cloud), on the public cloud (such as AWS, Azure, or Rackspace). Or with a combination of both, which is known as the hybrid cloud, thanks to the flexibility given by various virtualization solutions.
Therefore, You enter, launch virtualization on it, and create as many sessions on that system as you desire or are able.
Learn more about virtual machines here:
https://brainly.com/question/29535108
#SPJ1
802.11 is a series of standards to identify ____ networkswifi
Answers
IEEE 802 is a group of networking standards that covers the requirements for the physical and data-link layers of technologies like Ethernet and wireless. Local area networks (LANs) and metropolitan area networks must adhere to these requirements (MAN). IEEE 802 helps to ensure multi-vendor interoperability by encouraging vendors to adhere to standards.
How many channels in total are 802.11a wireless networks available?
The 5.75 GHz band, which contains a total of 23 channels, is used by 802.11a wireless.
What purposes do 802.11 standards serve?
It defines the collection of media access control (MAC) and physical layer (PHY) protocols for implementing wireless local area network (WLAN) computer communication. IEEE 802.11 is a subset of the IEEE 802 set of local area network (LAN) technical standards.
To know more about IEEE 802 visit;
https://brainly.com/question/13111560
#SPJ4
Write a program that prompts the user to enter his/her first name, last name, and year of birth in a single string (in the format: fn;ln;yyyy), then calculates the age tell it to him/her after greeting him/her using the first name.
Make sure to capitalize the user's first name, regardless of how he/she typed it in.
Hint: review Exercise 1!
Example:
Enter your first name, last name, and birth year (in format fn;ln;yyyy): alex;smith;1994
Hi Alex, you are 26 years old!
Answers
name = entry ("What is your name: ")
age = int("How old are you:")
year = 2014 - age + 100 print(name + "You'll turn 100 in the year " + str(year))
How does prompt programming work?An explicit request made by the software to the user in order to elicit data is known as a programming prompt. This usually takes the form of a question or prompt that the user must respond to before the software may continue to operate.
What sort of prompt comes to mind?When his friend did not answer his first question, he repeated, "Did you hear me?" Someone who was standing offstage had to prompt the actor. I was asked to enter a number by the computer.
To know more about prompt visit:-
https://brainly.com/question/29805090
#SPJ4
Write a function that checks whether your game character has picked up all the
items needed to perform certain tasks and checks against any status debuffs. Confirm checks with print statements.
Game Character has the following item list: [pan, paper, idea, rope, groceries]
Game Character has the following status debuffs: [slow]
Task 1: Climb a mountain – needs rope, coat, and first aid kit, cannot have slow
Task 2: Cook a meal – needs pan, groceries, cannot have small
Task 3: Write a book – needs pen, paper, idea, cannot have confusion
use python and explain the code
Answers
def __init__(self, nickname, weapons, weaknesses):
self.nickname = nickname
self.weapons = weapons
self.weaknesses = weaknesses
def get_model(self):
return self.nickname
def get_year(self):
return self.weapons
def get_color(self):
return self. weaknesses
def profile(self):
return self.nickname, self.weapons, self. weaknesses
player1 = character('','','')
player1.nickname = 'Dragon Slayer'
player1.weapons = ['pan', 'paper', 'idea', 'rope', 'groceries']
player1.weaknesses = ['slow']
for item in player1.weapons:
print("Item: ", item)
for debuff in player1.weaknesses:
print("Debuff: ", debuff)
CASE STUDY
Elmwood College
Situation:
The school is considering a new system that will speed up the registration process. As a system analyst, you are asked to develop a plan for fact-finding.
i) List all the possible techniques that you might use.
ii) Describe an advantage for each technique.
iii) Suppose the development budget is tight. How might that affect the fact-finding process?
iv)What are five important questions to use during fact-finding?
Answers
Write out every approach you might possibly employ. Interviews, document reviews, observation, and surveys are examples of potential methodologies.
What exactly do system analysts do?To aid programmers and architects in building computer systems, analysts draw diagrams. Computer system analysts, sometimes known as systems architects, examine the current computers systems and processes used by a business and develop new ones. These analysts make the company more productive in the process.
Are system analysts good at their jobs?Seems to be Systems Analysis a Salable Profession? Yes, if you want to work with networks of computers to boost efficacy and efficiency, being a systems administrator is a wonderful career choice.
To know more about system analyst visit:
https://brainly.com/question/29331333
#SPJ1
When you have backed into a parking space, you know your back end is close to but not over the paint line when you see the back paint line... a)-in the rearview mirror b)-in the middle of the front side c)-passenger mirror d)-disappear under the car e)-in the middle of the back side passenger windows
Answers
When you have backed into a parking space, you know your back end is close to but not over the paint line when you see the back paint line is in the middle of the back side passenger windows. The correct option is e.
What is a parking space?Due to their frequent use as the first and last mile of a journey, parking lots can play a significant role as a point of transition for drivers from their vehicles to other modes of transportation. In the design process, this gateway role is frequently disregarded.
They go by a variety of names, depending on the maker and location, including parking blocks, parking stops, and curb stops. No matter what name it goes by, the concrete or rubber stop erected at the front of parking spaces across the nation is known as a parking block.
Therefore, the correct option is e)-in the middle of the back side passenger windows.
To learn more about parking spaces, refer to the link:
https://brainly.com/question/13571646
#SPJ1
On Pinterest, a ________ is a collection of pins organized around themes, such as home decor, family, lifestyle, arts and crafts, style and fashion, travel, and food. Multiple Choice
a. pinlog
b. pinbook
c. pinfolio
d. look book
e. pinboard
Answers
On Pinterest, a pinboard is a collection of pins organized around themes, such as home decor, family, lifestyle, arts and crafts, style and fashion, travel, and food.
What is Pinterest?Pinterest is a social media and image sharing service based in the United States that allows users to save and discover information (specifically "ideas") on the internet through the use of images, and on a smaller scale, animated GIFs and videos, in the form of pinboards.
Ben Silbermann, Paul Sciarra, and Evan Sharp founded the website, which had 433 million global monthly active users as of July 2022. Pinterest, Inc., based in San Francisco, runs the site.
Pinterest is a visual search engine for ideas such as recipes, home and fashion inspiration, and so on. With billions of Pins on Pinterest, you'll never run out of creative ideas. Save Pins that you like to boards to keep your ideas organized and easy to find.
Learn more about Pinterest
https://brainly.com/question/14019061
#SPJ1
What type of error occurs in this program?
listA = [10, 3, 11, 4, 1]
num1 = listA[2]
num2 = listA[8]
sum = num1 + num2
print(sum)
A. Logic Error
B. Runtime Error
C. List Error
D. Syntax Error
Answers
Answer:
Explanation: C. Runtime Error
By looking at the code snippet, the error occurs on line 3:
num2 = listA[8]
The reason for this is because listA only has 5 elements in it. In order to be able to access listA[8], listA would have to have at least 9 elements inside of it, which it does not.
In Python, this would raise an IndexError which is a type of Runtime Error.
Answer: B. Runtime Error
Explanation:
I think you are wrong on this num2 = listA[8]! It would cause Runtime Error that why I pick B!
Which method adds 10 to the right end of the array?
myArray.
(10)
add
index
append
insert
Answers
If an array element cannot be found, the indexOf() function returns -1. It returns the first index of the element's occurrence.
Which approach searches an array for the very first instance of 10?The indexOf() method uses rigorous equality (the same algorithm as the === operator) to compare searchElement to array items.In sparse arrays, the indexOf() technique leaves empty spaces unfilled.The method indexOf() is general.Only a length property and properties with integer keys are required for this value.The indexOf() method returns the array element's initial index of occurrence, or -1 if it cannot be found.An element's position inside the array is indicated by its index, which can either be a number or a field with a number (beginning at 1).When you give an array name and index, the following guidelines apply:The name of the array must be a distinct symbolic name.
To learn more about array refer
brainly.com/question/28061186
#SPJ1
Match the following extinguisher picture icons with their corresponding types of fire they can be used to extinguish. (Click an item on the left, then click its matching item on the right.)
a. blue - Energized electrical equipment including fuse boxes, computers, copiers, wiring, and control panels
b. green - Ordinary combustibles including wood, paper, cloth, rubber, and many plastics
c. red - Flammable liquids and gases including, gasoline, solvents, propane, and paints
d. black - Cooking oils and fats
Answers
Fuse boxes, computers, copiers, cables, and control panels are examples of energized electrical equipment that is colored blue. Regular combustibles including wood, paper, fabric, rubber, and many types of plastics are considered green. Gasoline, solvents, propane, paints, and other flammable liquids and gases are all marked in red. Oils and fats for cooking are black.
The meaning of the symbols on a fire extinguisher?To identify the sort of fire that should be extinguished, use the labels A, B, C, or D. The majority of fire extinguishers will have a pictogram label on them indicating the kind of fires they are intended to put out.
What is the Class C fire symbol?The C classification denotes the non-conductive nature of the extinguishing agent. A blue circle serves as the graphic representation of Class C.
To know more about extinguish visit :-
https://brainly.com/question/20436548
#SPJ1
when you use the reuse slides pane, you can insert slides from another presentation or from a sharepoint server. which of the following is the name for the slides stored on a sharepoint server?
Answers
The term "slide library" refers to the collection of slides kept on a SharePoint server.
Which view shows each slide's thumbnail on the screen individually?All of the slides in your presentation are shown in the Slide Sorter view (below) as horizontally arranged, thumbnails.
What is the term for a group of data that is arranged in cells in a grid of columns and rows?A worksheet, commonly referred to as a spreadsheet, is made up of cells where you can enter and compute data. There are columns and rows separating the cells. Workbooks are where worksheets are constantly kept.
To know more about slides visit:-
https://brainly.com/question/20777311
#SPJ4
At the current rate of increase what are clock rates now projected to be in 2025
Answers
At the current rate of increase, the clock rate now projected to be in 2025 is 10 GHz.
What are clock rates?In computing, clock rate or clock speed often refers to the frequency at which a processor's clock generator can create pulses.
The fact that the speed of light is the ultimate limit on the speed of electrical communications has constrained the rate of increase of the clock rate. Architects are exploiting the extra transistors to boost processor speed by adding more cores.
Therefore, at the current rate of increase, the clock rate in 2025 is expected to be 10 GHz.
To learn more about clock rates, refer to the link:
https://brainly.com/question/28592956
#SPJ1
Type the correct answer in the box. Spell all words correctly.
What is a society that has moved to the Internet rather than relying on physical media called?
A society that has moved to the Internet rather than relying on physical media is called a
Answers
Network society is a term that was first used in 1991 to describe the social, political, economic, and cultural changes brought on by the proliferation of networked, digital information and communications technology.
What exactly is tangible media?Physical media are tangible items that are used to store or send data during data transfers. Typically, these physical media are tangible items composed of materials like glass or copper. They have physical characteristics like weight and color, and they can be touched and felt.
What three sorts of physical media are there?On this page, three different physical layer network media types for data transmission will be discussed, along with their benefits and drawbacks. Copper cable, wireless technology, and other basic physical layer media types will be discussed.
To know more about physical media visit :-
https://brainly.com/question/29451122
#SPJ1
Choose all the correct statements about Persistent Connections.
The original version of HTTP (1.0) established Persistent Connections.
The client and server can exchange multiple request/response messages over the same TCP connection.
The slow start phase for each page can be avoided.
Persistent connections require webserver to keep a connection open for a certain number of seconds, which will always increase the total performance benefits.
Answers
Persistent Connections is a feature of the original version of HTTP (1.0) that allows the client and server to exchange multiple request/response messages over the same TCP connection.
Choosing the correct statements about Persistent Connections:The original version of HTTP (1.0) established Persistent Connections.The client and server can exchange multiple request/response messages over the same TCP connection.The slow start phase for each page can be avoided.The original version of HTTP (1.0) established Persistent Connections, which allows the client and server to exchange multiple request/response messages over the same TCP connection. This feature helps to avoid the slow start phase for each page, providing a significant performance benefit. Persistent Connections have become a standard in web communication, and are used in all modern versions of HTTP.
Learn more about Web Browser: https://brainly.com/question/28875018
#SPJ4
this feature offered by mutual funds allows investors to switch from one mutual fund to another within a fund families.
Answers
The feature is called Fund Switching, also known as exchange privileges.
What is fund switching?
This feature is called "fund switching" or "exchange privileges." It allows investors to move their investment from one mutual fund to another within the same fund family without incurring a sales charge or fee.
Fund switching is typically offered by mutual fund companies as a way to give investors flexibility and control over their investments. It allows investors to respond to changing market conditions or to rebalance their portfolios without incurring additional costs.
Some mutual fund companies may impose certain restrictions on fund switching, such as limiting the number of exchanges that can be made within a given time period.
It is important for investors to understand these restrictions and to carefully consider their investment decisions before making any changes to their portfolios.
To Know More About Mutual Funds, Check Out
https://brainly.com/question/9965923
#SPJ1
In general, you should use class variables only for symbolic constants or to maintain data held in common by all objects of a class.
True
Answers
In general, class variables should be used only for symbolic constants or to keep data shared by all objects in a class. (True)
What is symbolic constants?When someone mentions "constants" in any programming language, the majority of people immediately think of symbolic constants. Throughout a program, a fixed value is simply represented by a label or name, and this is what is meant by a "symbolic constant." As an illustration, the number 3.14159 could be defined as PI, a constant.
You can define a symbolic constant by using it as a label or as a.set statement. By assigning it a value, a symbol can be used as a constant. Instead of using the value itself, the value can then be referenced by its symbol name. If a value appears frequently in a program, using a symbol as a constant is practical.
Learn more about symbolic constant
https://brainly.com/question/12020720
#SPJ4
in the united kingdom, the metropolitan police service established the fingerprint bureau in 1901, and by the end of the century, over 250 million fingerprints had been recorded in their database.
Answers
In July 1901, New Scotland Yard (Metropolitan Police) established the fingerprint branch. It made use of the Henry system for classifying fingerprints.
When did police utilize fingerprints for the first time?Inspector Eduardo Alvarez created the first criminal fingerprint identification in Buenos Aires, Argentina in 1892. Francisca Rojas, a woman who killed her two boys and then cut herself in an effort to shift the responsibility, was recognized by him.
What is the fingerprint's past?Galton invented the fingerprinting system first. Sir William J. Herschel's work, which collection began in 1857 when he forcibly pushed a building supplier to put his handprint on the back of a contract in order to avoid paying, served as the inspiration for his three-point identification method.
To know more about fingerprint visit:-
https://brainly.com/question/15221897
#SPJ4
In C, write a recursive function int Palindrome(char mystr[], int len) that checks whether the string char mystr[]="....." is a palindrome or not. If it is then print "Palindrome" and if not print "Not palindrome" to the console. A string being a palindrome has 2 cases:(i)if the string has an even length, then the first half is a mirroring of the second half; e.g., abccba is a palindrome, whereas abccab is not. (ii) if the string has an odd length, then disregard of the letter in the middle, the first half is a mirroring of the second half; e.g., abcvcba is a palindrome, whereas abccvba is not.
Answers
#include <stdio.h>
#include <string.h>
int Palindrome(char mystr[], int len)
{
// base case: if the length of the string is 0 or 1, it is a palindrome
if (len <= 1)
return 1;
// check if the first and last characters are the same
if (mystr[0] != mystr[len - 1])
return 0;
// if the first and last characters are the same, check the substring that
// lies between them (excluding the first and last characters)
return Palindrome(mystr + 1, len - 2);
}
int main()
{
char mystr[] = "abcba";
int len = strlen(mystr);
if (Palindrome(mystr, len))
printf("Palindrome\n");
else
printf("Not palindrome\n");
return 0;
}
This function works by checking the first and last characters of the string. If they match, it calls itself with a substring that excludes the first and last characters. This process continues until the length of the string is 0 or 1, at which point it returns 1 (indicating that the string is a palindrome). If any of the characters do not match, the function returns 0 immediately.
read more about this at https://brainly.com/question/12567947
#SPJ4
you are investigating the use of website and url content filtering to prevent users from visiting certain websites.
Answers
Website filtering typically increases bandwidth availability and can be used to enforce the company's internet usage policy.
Threatening emails are prevented from being delivered by spam blockers. Virus blockers isolate and remove malicious information. Anti-phishing software searches content for phishing attempts and removes them, guarding against outside efforts to get private data.
Which anti-web threat software prevents users from accessing blocked websites?
virus defenders impedes the delivery of unsolicited mails to your network gateway anti-spam software prevents access to websites that are prohibited.
Which of the following is the best approach to enabling internet access to private resources?
A VPN offers a safe external connection to the resources of an internal network you can put a VPN server inside the DMZ.
To know more about Website filtering visit;
https://brainly.com/question/23440115
#SPJ4
challenge activity 10.1.1: enter the output of modules. 401468.2415682.qx3zqy7 type the program's output main.py arithmetic.py import arithmetic def calculate(number): return number - 3 print(calculate(2)) print(arithmetic.calculate(2)) -1 6
Answers
The output will be 200, 42 for the given program.
What is a program?Source code is the name given to a computer program that can be read by humans. Because computers can only run their native machine instructions, source code requires the assistance of another computer program to run.
As a result, the compiler of the language can convert source code into machine instructions. (An assembler is used to translate machine language programs.) An executable is the name given to the finished file. As an alternative, source code could run through the language's interpreter.
The operating system loads the executable into memory and launches a process if it is asked to be executed. In order to fetch, decode, and then execute each machine instruction, the central processing unit will soon switch to this process.
Learn more about programs
https://brainly.com/question/26134656
#SPJ4
A programmer is debugging a puzzle game they have just created. As they
test the game, they enter inputs that they know to be incorrect. Is this a good
strategy for debugging a game?
O
A. No, because errors in correct answers are the most likely to be
overlooked
B. Yes, because entering the wrong answers can help uncover errors
that were overlooked
OC. No, because entering the wrong answers is not likely to test the
game's limits
D. No, because players are less likely to notice errors when they enter
wrong answers
Answers
Answer:
the answer is yes
Explanation:
this is b because when they input wrong texts it brings out the errors that were initially there
Briefly describe how data is transferred from host 1 to host 2 through a router. remember to explain the encapsulating of data.
Answers
Encapsulation, in general, is the act of gathering related code into a single location.
How is data transported in a router?A router connects network devices by sending data packets between them, to put it simply. This data might be transmitted online or from one device to another. The router achieves this by assigning a local IP address to each networked device.
Encapsulation is a method for preventing users from getting state values for all of an object's variables by limiting direct access to some of its components. Both data members and data functions or methods connected to an instantiated class or object can be hidden using encapsulation.
To learn more about Data transfer Router Refer:
brainly.com/question/14457240
#SPJ4
Imagine a scenario where new child classes are introduced frequently from a base class. The method calling sequences for every child class are the same but the implementations are different among the child classes. Here which design pattern would you like to apply? Explain the reasons with examples
Answers
The Template Method design pattern seems like a suitable fit in this situation.
What is template method design?Template method design is defined as a behavioral design approach that allows subclasses to override particular parts of an algorithm without altering the algorithm's overall structure. When you wish to allow clients to expand only specific steps of an algorithm but not the entire method or its structure, use the Template Method pattern.
With specific stages defined as abstract methods, this pattern defines the basic structure of an algorithm in a base class. Subclasses can then offer their own implementation for each stage by overriding these methods.
Thus, the template method design pattern seems like a suitable fit in this situation.
To learn more about template method design, refer to the link below:
https://brainly.com/question/15584332
#SPJ1
The ____ option instructs the ls command to provide a listing of information about the directory itself, not its contents.
Answers
The -d option instructs the ls command to provide a listing of information about the directory itself, not its contents.
A command is a directive or instruction that is given to a computer to perform a specific task. In the context of a computer operating system or application, a command is a specific instruction that tells the computer to perform a particular action or function.
The example of -d option instructs the ls command is:
$ ls -d /path/to/directory
This will display information about the directory /path/to/directory, rather than a listing of the files and directories contained within it.
You can also use --directory as an alternative to -d, like this:
$ ls --directory /path/to/directory
Learn more about command, here https://brainly.com/question/16268451
#SPJ4
You have decided to implement Gigabit Ethernet on your network. Each switch port is connected to a single device. Following the installation, you will find one device connected to a switch that is only running at 100 Mbps.
Answers
The term for "You've decided to upgrade your network to Gigabit Ethernet. Every switch port is linked to a single device. Following installation, you will discover one device linked to a switch that is only capable of 100 Mbps.", is crosstalk.
Crosstalk is unwanted signals in a communication channel (like in a telephone, radio, or computer) created by energy transference from another circuit (as by leakage or coupling): discourse that is unrelated to the main issue being addressed.
Crosstalk creates mistakes or hinders data transfer by causing interference on an afflicted pair of conductors or the entire connection. Have you ever overheard someone else's phone call, for example? Interference between neighbouring telephone cables causes this.
In fact, there are two forms of crosstalk and two potential sources of crosstalk in any system. Crosstalk is classified into two types: near-end crosstalk and far-end crosstalk, both of which cause undesired interference between signals on distinct interconnects.
Learn more about crosstalk here https://brainly.com/question/28111008
#SPJ4